Gone Phishing with Go Phish
A basic phishing attack is one of the easiest and least technical social engineering attacks to perform. Crafting a fraudulent email and replicating a website is something anyone with basic knowledge of computers can do. The Social Engineering Toolkit (SET) makes this process even easier by guiding the attacker through the process. SET contains many tools for targeted attacks against a singular person or organization. Phishing is just one attack vector in the toolkit.
Introduction
Gophish, self-described as an open-source phishing framework, is a more pleasant program to work with for large and long-term phishing attacks. The interface offers some very cool features such as reporting victim activity, a feature-rich dashboard for viewing statistics about a campaign, and an API to automate the process.
Setup
Setup takes mere seconds. Just download the file from the github page and unzip it to any directory.
For ease of testing, in the config file, set the listen url to 0.0.0.0 so that it listens everywhere. It will look like:
{
"admin_server" : {
"listen_url" : "0.0.0.0:3333",
"use_tls" : false,
The gophish file needs to be executable so run:
chmod +x gophish
Gophish hosts pages on ports 80 and 3333 so before running the executable, any other webserver on port 80 needs to be turned off. For apache, I ran:
sudo service apache2 stop
After executing the gophish file, navigate to the machine on port 3333. Default login credentials are admin : gophish.
Your First Campaign
The Sending Profile
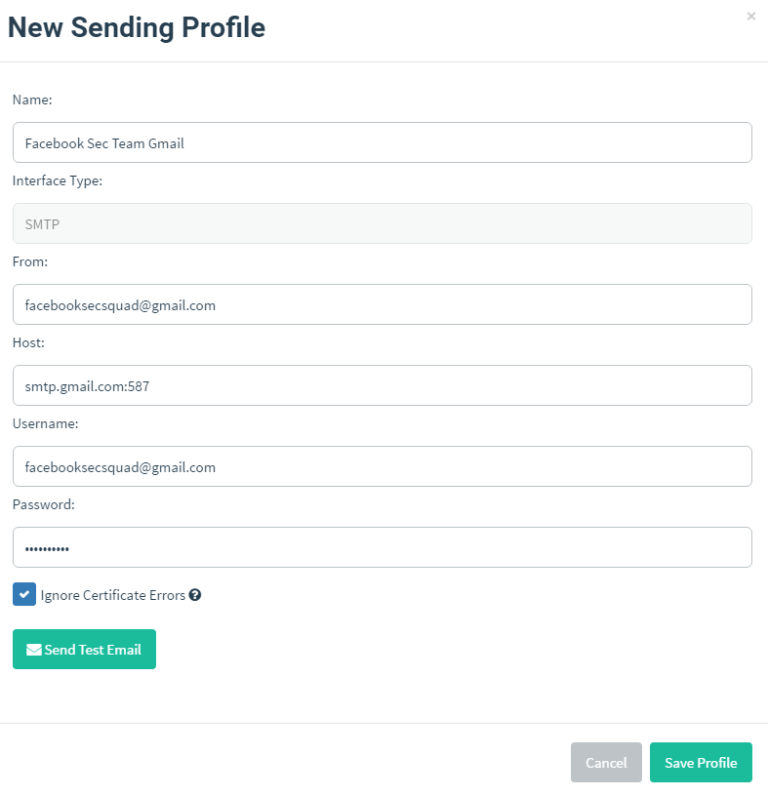
A sending profile is the email account and server that send the emails. For this campaign I made a Gmail account and used Google’s SMTP server.
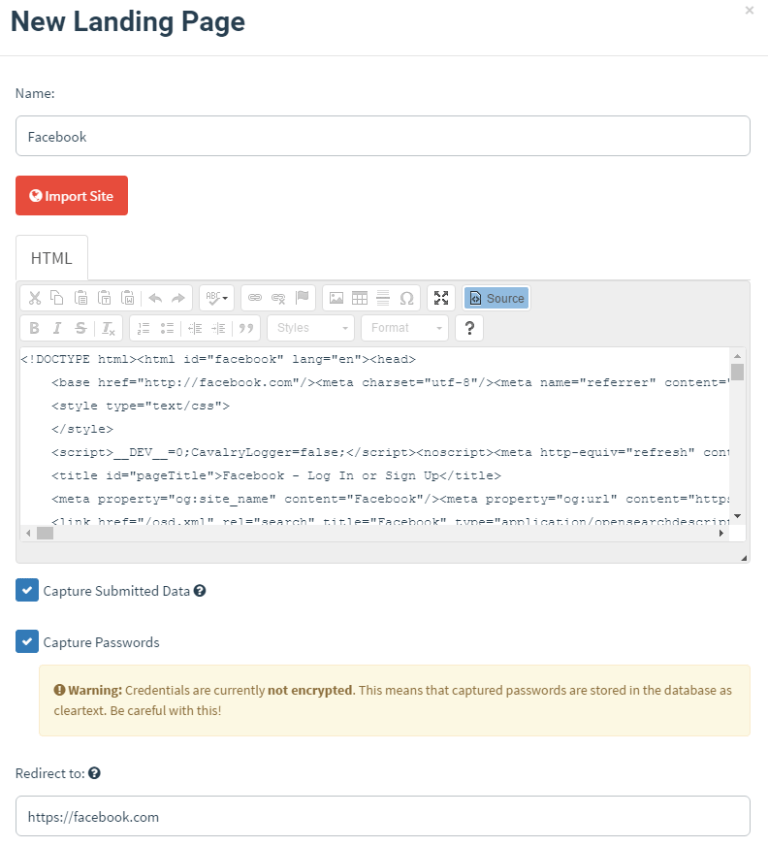
This is the cloned page on our server that users be linked to in the email and log in to before being redirected. Cloning a page is as simple as clicking import and typing the URL. The HTML will appear in case you want to alter anything. Options will also show up to capture submitted data and passwords.Finally, choose the actual site to redirect to after login.
The Email Template
Here’s where we’ll work our crafty social engineering skills. Gophish does not offer templates already typed, but just like importing site templates, the same can be done for emails.If you’ve received an email from LinkedIn, Facebook, or whatever site you clone, you can use it as a template. Many clients such as Gmail have the option to view the raw source of an email. Just copy it and paste it in.
Another very cool feature of Gophish is the ability to track user actions after sending. Selecting Add Tracking Image will allow you to see if each user has opened the email.
Personalizing a phishing email greatly increases the chances of success. Gophish implements several variables to use in the email template. One example from the documentation is:
{{.FirstName}},
The password for {{.Email}} has expired. Please reset your password here.
Thanks,
Morning Catch IT Team
The Users
After creating a new group, we will assign those variables for users. Each user can have a first and last name, email, and position. If you have a large set of users in a spreadsheet, it’s also possible to import from a CSV file.
Putting It All Together
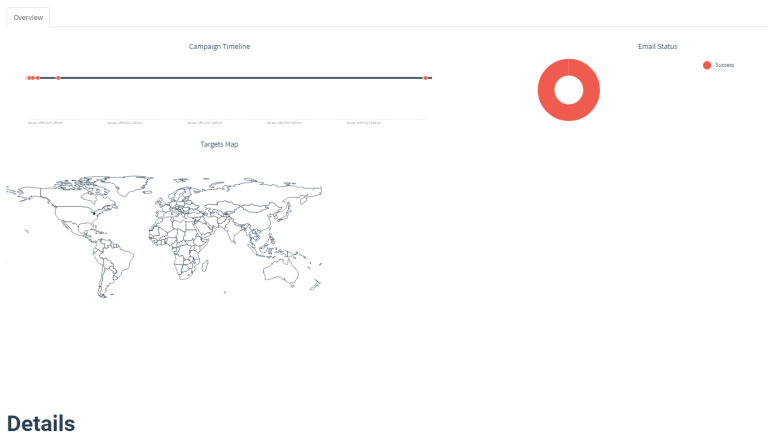
Creating a campaign is as easy as selecting all of the above parts we just created. Input the public IP address of your machine and make sure it is accessible over port 80. Finally, select a time if you want to schedule it for the future and hit launch. The dashboard will show the status of each email and user afterwards.
Conclusion
Gophish is incredibly fast to get up and running and has a beautiful UI. I have not tried the API, but they claim campaigns can be automated with any programming language using the RESTful API. Of all the phishing software out there, Gophish seems to be a well put together and full-featured program.
